Server monitoring plays a pivotal role in maintaining a stable and high-performing IT infrastructure. In today’s digital landscape, where businesses rely heavily on online services and applications, any server downtime or performance degradation can have far-reaching consequences.
Effective server monitoring isn’t solely about keeping tabs on hardware; it’s about gaining insights into your server’s behavior and performance. This proactive approach helps prevent potential issues before they disrupt your operations, enabling you to make informed decisions, allocate resources efficiently, and optimize server performance. In essence, server monitoring is a cost-effective investment that can save your organization time, money, and the headache of dealing with unexpected server problems.
To gain a comprehensive understanding of server monitoring, let’s look at the essential parameters and metrics that should be part of your monitoring strategy. These metrics provide valuable insights into your server’s health, allowing you to take timely actions to maintain a stable IT environment.
CPU Usage:
Metric: Percentage of CPU utilization.
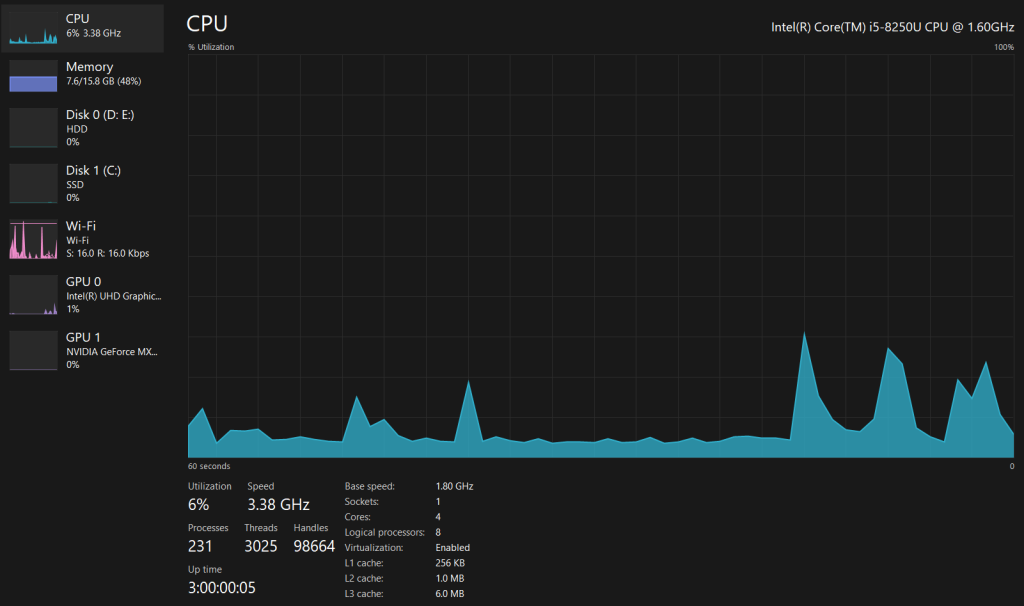
Importance: High CPU usage can lead to performance bottlenecks, causing applications to run slowly or become unresponsive. It’s essential to monitor this metric to ensure your server has adequate processing power to handle the workload effectively. A sudden spike in CPU usage may indicate a performance issue or a resource-intensive process that needs attention.
Memory Usage:
Metric: Memory utilization, including both physical RAM and swap space.
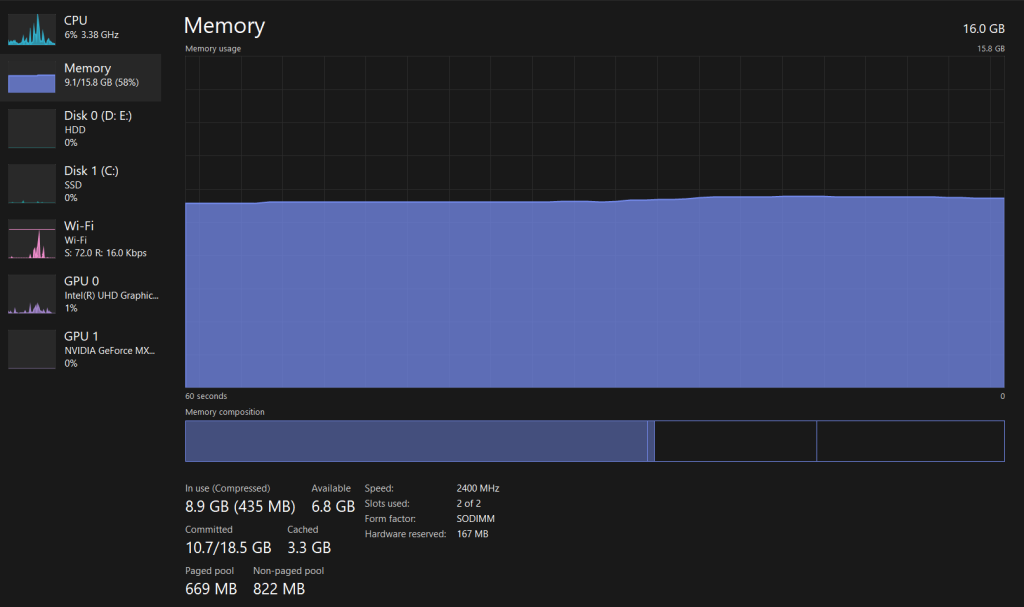
Importance Insufficient memory can result in slow server response times and even crashes. Monitoring memory usage helps identify potential resource constraints. When memory usage consistently approaches or reaches its limits, it’s a sign that your server may need additional RAM or that there could be memory leaks in your applications.
Disk Space:
Metric: Available disk space on all storage devices.
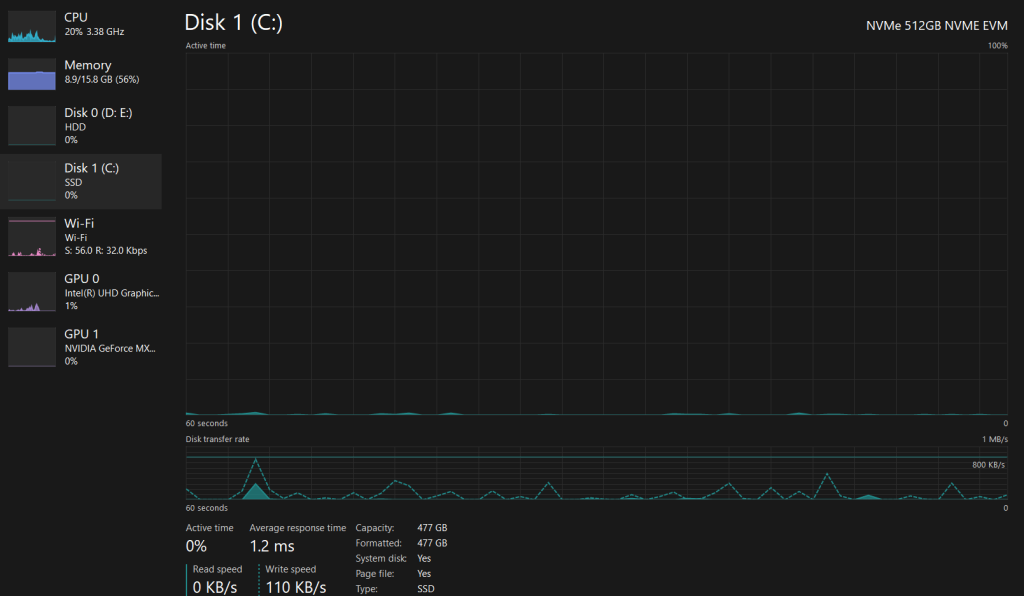
Importance: Running out of disk space can disrupt server operations and cause data loss. Regularly check and maintain disk space to prevent such issues. Monitoring disk space also helps you identify any rapidly growing log files or unnecessary files that could be safely deleted to free up storage capacity.
Network Throughput:
Metric: Data transfer rates (in Mbps or Gbps).
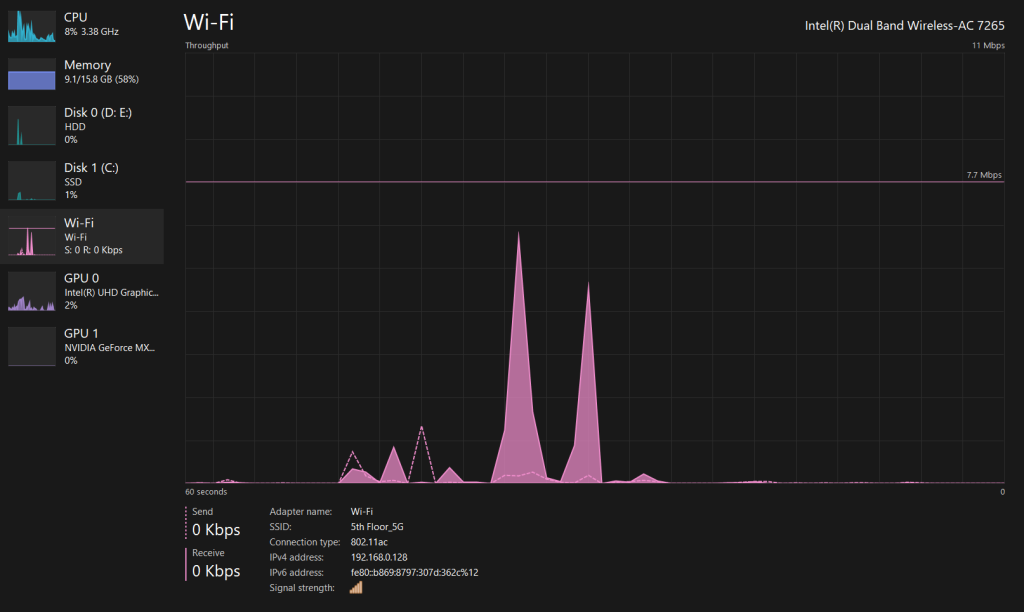
Importance: Monitoring network throughput ensures that your server can handle incoming and outgoing data efficiently, preventing network congestion. Slow network throughput can lead to delays in data transmission, affecting user experience and application performance. It’s crucial to monitor and optimize network performance to maintain smooth data flow.
Response Time:
Metric: Server response time in milliseconds.
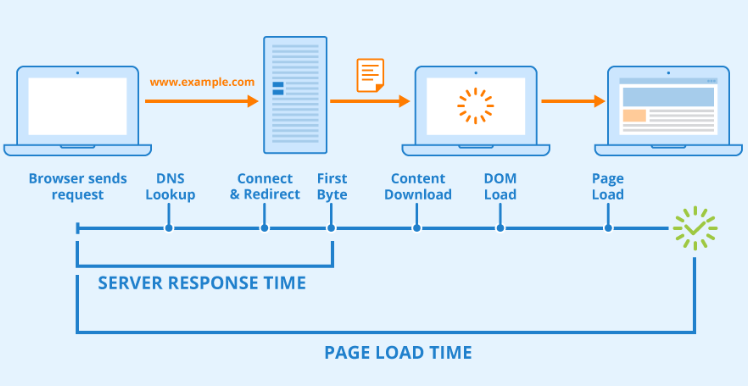
Importance: Response time directly impacts user experience. The sluggish response can frustrate users and lead to a loss in business. Monitoring response time helps you identify performance bottlenecks, whether they are caused by server issues or application inefficiencies. Faster response times lead to better user satisfaction and retention.
Error Rates:
Metric: The frequency of server errors (e.g., 404 or 500 errors).

Importance: High error rates can indicate underlying issues in your server or applications, affecting user satisfaction. Monitoring error rates helps you promptly detect and address problems, reducing the impact on users. It also aids in troubleshooting and identifying patterns of errors that require attention.
Uptime/Downtime:
Metric: Total uptime and downtime percentages.
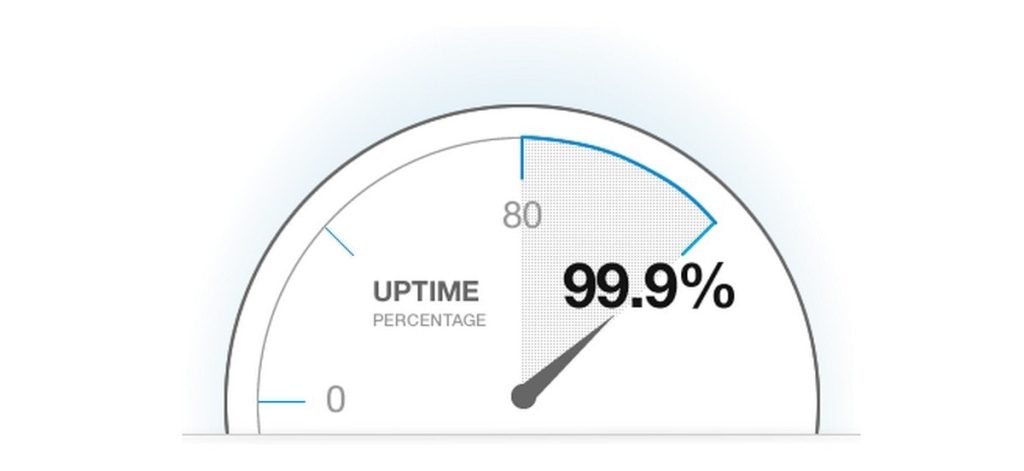
Importance: Tracking server uptime is crucial to ensuring the availability of your services. Downtime can result in lost revenue, damage to your reputation, and inconvenience for users. Monitoring uptime and downtime allows you to proactively address issues and implement redundancy and failover measures to minimize service interruptions.
Security Events:
Metric: Number of security events, including failed login attempts and intrusion attempts.

Importance: Monitoring security events helps detect potential breaches and vulnerabilities, allowing you to take prompt action to secure your server. By analyzing security event data, you can identify patterns of suspicious activity and strengthen your server’s defenses against cyber threats.
Application Performance:
Metric: Metrics specific to your applications, such as transaction times, database query speeds, and user session data.

Importance: Application performance directly impacts user satisfaction. Monitoring these metrics ensures your applications run smoothly and respond promptly to user interactions. It allows you to pinpoint performance issues within your applications and optimize them for a seamless user experience.
Resource Trends:
Metric: Historical data and trends for network parameters.
Importance: Analyzing trends in resource usage helps identify long-term resource requirements and allows for proactive resource allocation. By studying resource trends, you can make informed decisions about server upgrades, capacity planning, and resource optimization, ensuring that your server remains efficient and cost-effective over time.